Cvss Is Useful to Describe How an Attack Works
This review surveys the current research in applying ML to fuzzing. Vault status command works when a namespace is set.
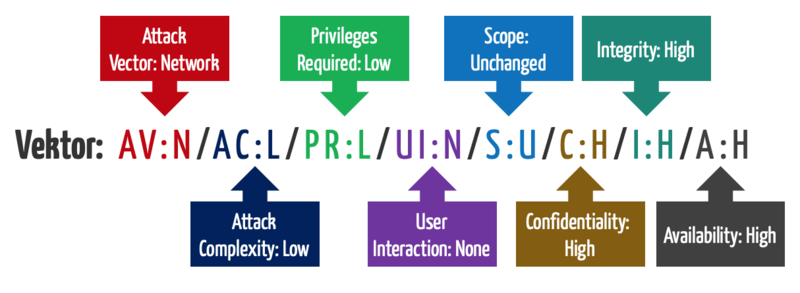
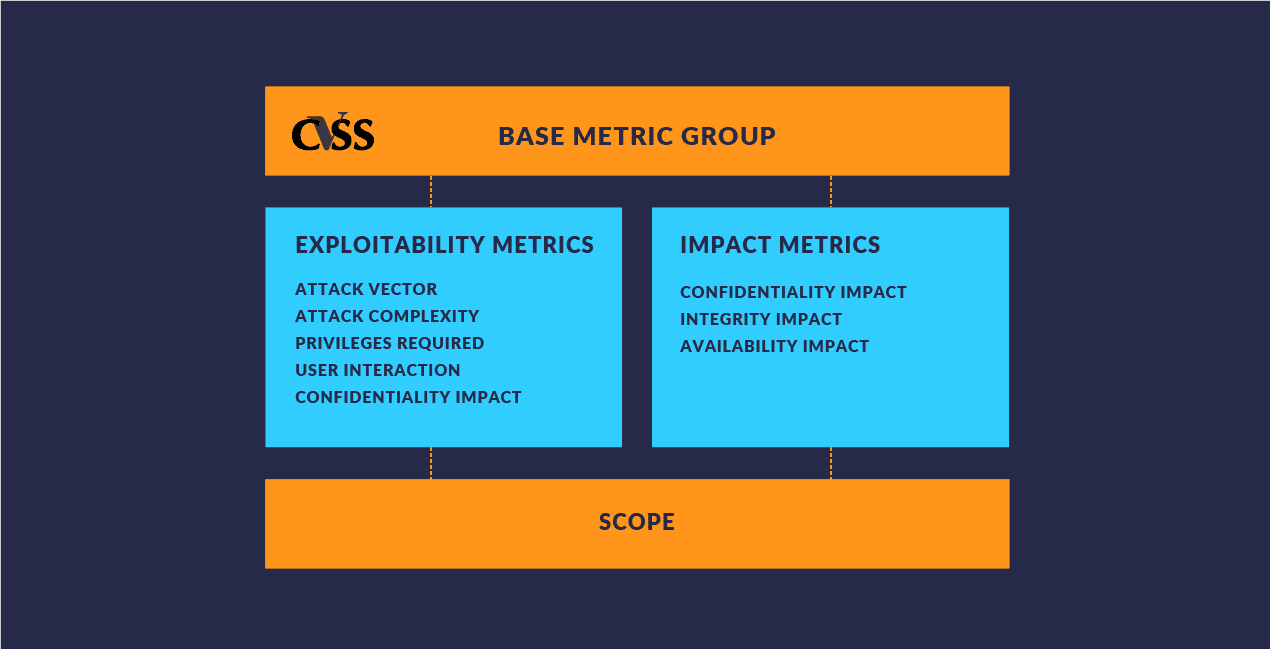
Cvss Common Vulnerability Scoring System It Security
It also includes command-line SFTP and SCP.
. I want ot configure all my Cisco IOS Komutları ntp master 1 R2config ntp server 10. We will take care of all your assignment needs. Últimas noticias fotos y videos de Perú y el mundo en El Comercio Perú.
We provide assignment help in over 80 subjects. Your switch may have an NTP server turned on. The PoC works on all supported versions of Windows.
New telemetry metrics reporting lease expirations by time interval and namespace. Alignment to the NIST SP 800-181 Cybersecurity Workforce Framework Category Specialty Area Work Roles. You previously captured packets using the tcpflagssyn1 and tcpflagsack1 filter but only saw a few SYN-ACK packets.
Después de buscar el nombre de Bluetooth haga clic manualmente en el nombre de Bluetooth para emparejarlo automáticamente sin contraseña. Ladresse IP est un numéro. Version 2 of log4j between versions 20-beta-9 and 2150 is affected.
Moreover as the tool is free you will be able to scan the vulnerabilities of different networks quite quickly. 0 International License and code samples are licensed under the BSD License. Added vault operator usage command.
Specifically this review discusses successful applications of ML to fuzzing briefly explores challenges encountered and motivates future research to address. 1 Fan site of Diablo 2 and a source of vast information. After examining the wireshark results shown in the image which of the.
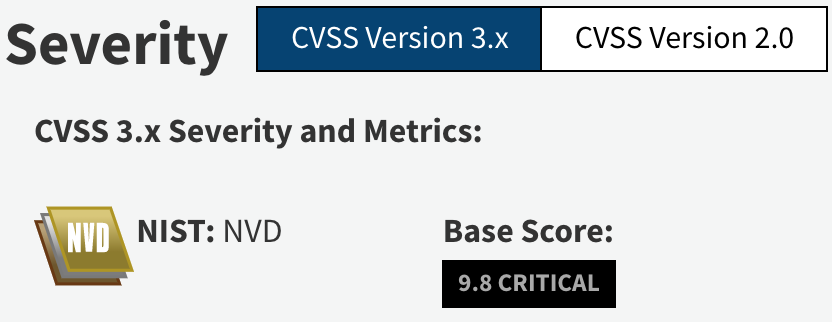
This vulnerability allows an attacker to perform a remote code execution on the vulnerable platform. It is the best choice for developing Bluetooth audio solutions. The log4j vulnerability CVE-2021-44228 CVE-2021-45046 is a critical vulnerability CVSS 31 base score of 100 in the ubiquitous logging platform Apache Log4j.
All your academic needs will be taken care of as. A DDoS Distributed Denial-of-Service attack is very similar to a DoS Denial-of-Service attack with the only difference being that the same attack is carried out by many different people or botnets at exactly the same time. Level 2 - Intermediate.
You are using wireshark to try and determine if a DoS attack is happening on your network 1282811. It is also useful for knowing the resulting offset using the exact time of 1a. Update Trial Enterprise license from 30 minutes to 6 hours.
You have now changed the filter to tcpflagssyn1 and tcpflagsack0. You can request for any type of assignment help from our highly qualified professional writers. By performing this regular test rhythm during 5 days the Holiday-Nin- ja-Pass is also valid on days 6 and 7 without further proof of testing.
03182008 Consider switching to the Firefox Web browser with the NoScript plug-in. We are a leading online assignment help service provider. The first command ntp server configures your Cisco device to use the specified NTP server.
Choking Heart attack Poisoning. Plant innate immunity and early leaf senescence share molecular components. Bluetooth sound bar.
Describe how principles are applied to create ethical transparent and fair AI. Recent research in fuzzing has focused on applications of machine learning ML offering useful tools to overcome challenges in the fuzzing process. Added active since timestamp to the status output of.
Cvss Scores To Measure Mobile App Risk Nowsecure
What The Heck Is Cvss Part I Techkranti

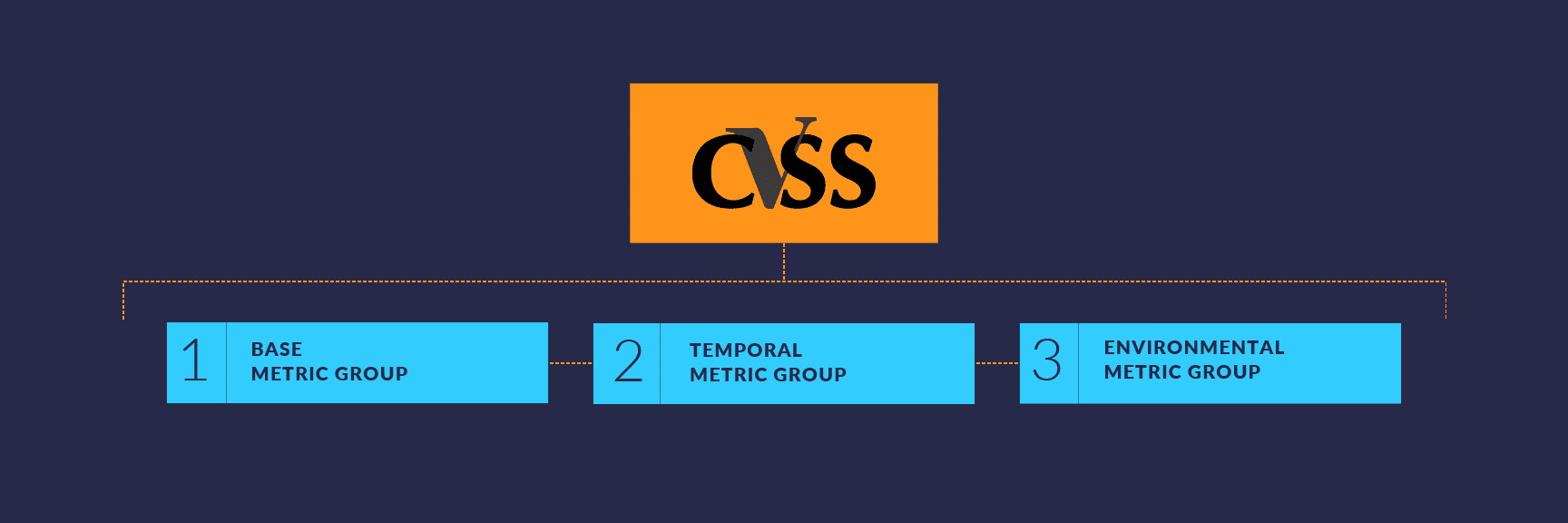
Make Cvss Scores Work For Your Risk Management Program

Industrial Cvss Alternative Calculations For Different Needs Incibe Cert
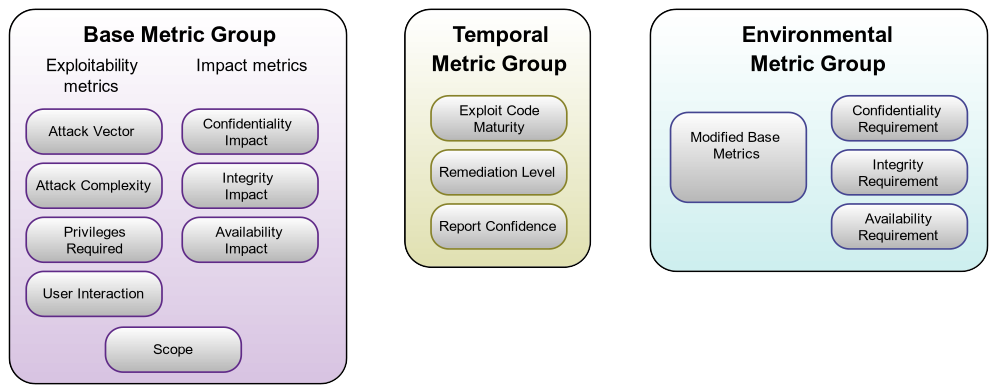
Page 2 Of The Overview Of Common Vulnerability Scoring System Cvss Part 03 Huawei Enterprise Support Community
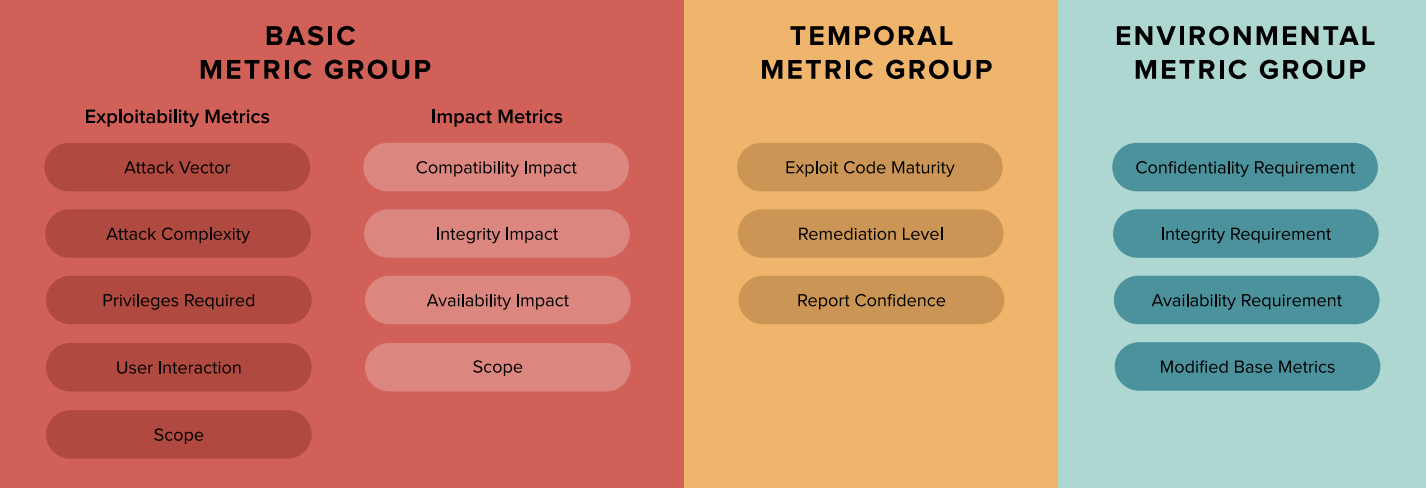
The 3 Reasons Cvss Scores Change Over Time Balbix

Cvss Everything You Need To Know About Common Vulnerability Scoring System Appsealing

Common Vulnerability Scoring System Cvss Risk Management Scoring System Vulnerability
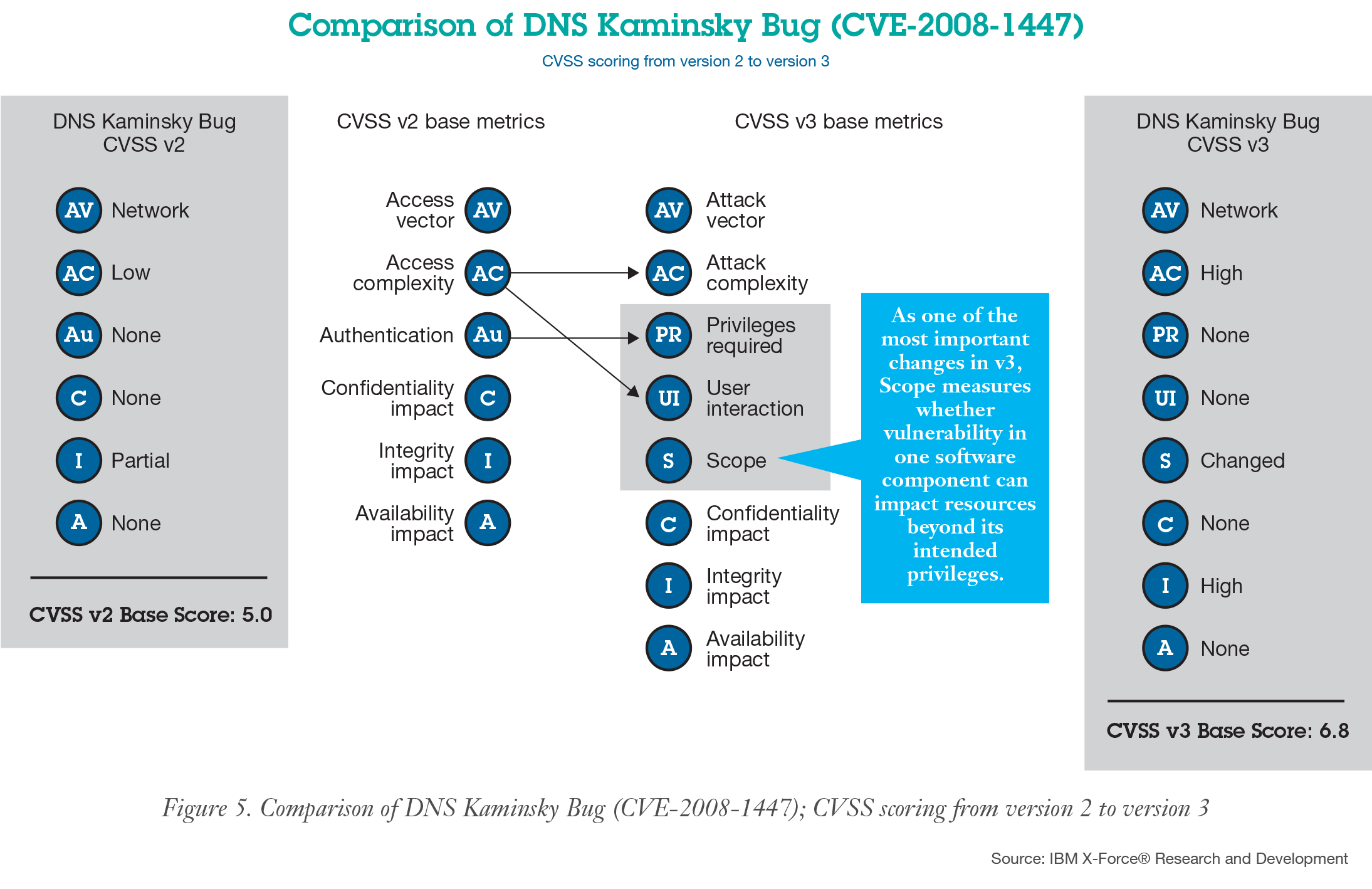
Markdown Designer Vulnerabilities Get A Fresh Cvss V3 Look
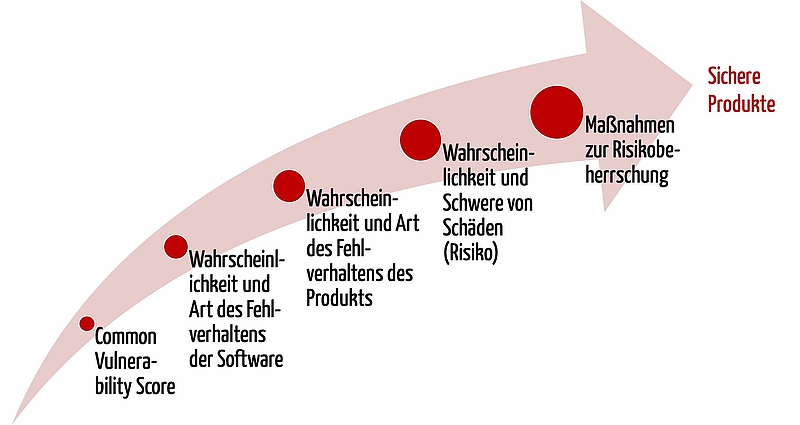
Cvss Common Vulnerability Scoring System It Security

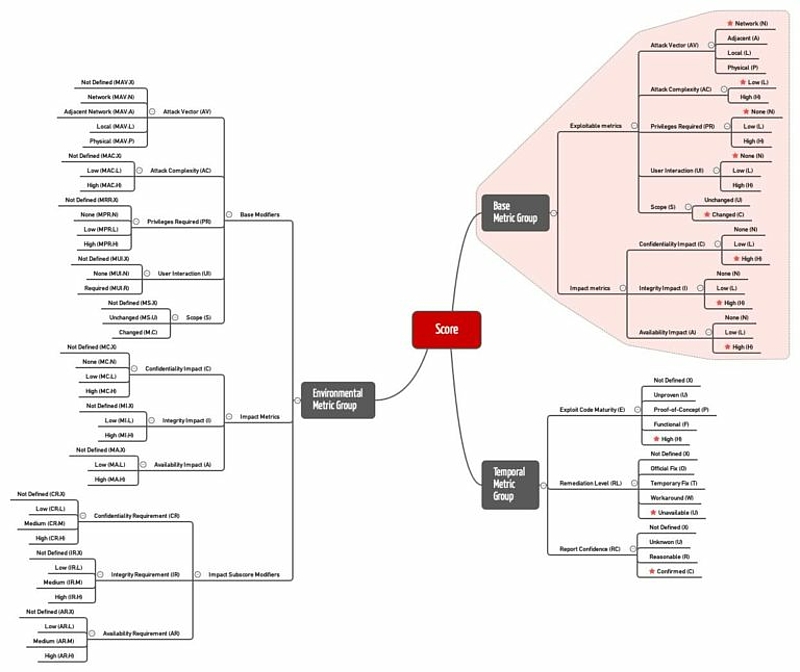
Cvss V3 Metric Groups Source First 2015 Download Scientific Diagram

Cvss Common Vulnerability Scoring System It Security
Cvss Scores To Measure Mobile App Risk Nowsecure
Using Cvss For Pentest Reports

Cvss Scores A Practical Guide For Application Zerofox

Understanding Vulnerability Scoring Cvss Explained

2021 01 19 Summary Of Latent Feature Vulnerability Rankings Of Cvss Vectors


Comments
Post a Comment